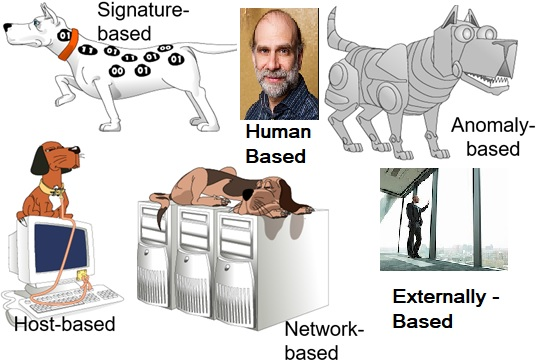
The best way to detect precursors to data exfiltration is to employ a six-prong detection approach applied to all risk areas as practicable. Figure 1. shows the six-pronged detection approach.
Figure 1. Six-Pronged Data Exfiltration Precursor Detection Approach [1] [2].
1) Signature Based.
Characteristics: 1) Uses known pattern matching to signify attack; 2) Former zero days, known exploits, etc.
Advantages: 1) Widely available; 2) Most antivirus is based heavily on this; 3) Fairly fast; 4) Easy to implement; 5) Easy to update.
Disadvantages: 1) Cannot detect attacks for which it has no signature – Zero days; 2) Insider threat.
2) Host Based.
Characteristics: 1) Runs on a single host; 2) Can analyze audit-trails, logs, the integrity of files and directories, etc.
Advantages: 1) More accurate than NIDS; 2) Less volume of traffic so less overhead.
Disadvantages: 1) Deployment is expensive; 2) No plan for if the host gets compromised – Real risk for organizations with more than 10 thousand employees.
3) Human Based [2].
Characteristics: 1) Has the unique experience set deriving intuition; 2) Has five senses.
Advantages: 1) Has the ability to learn multiple tools and connect the dots; 2) Can set team direction and inspire people; 3) Can think creatively; 4) Can think with the voice of the customer or recipient of a phishing e-mail.
Disadvantages: 1) Bias and ego; 2) Cannot calculate large numbers fast.
4) Anomaly Based.
Characteristics: 1) Uses statistical model or machine learning engine to characterize normal usage behaviors; 2) Requires big data and other software tools; 3) Recognizes departures from normal as potential intrusions.
Advantages: 1) Can detect attempts to exploit new and unforeseen vulnerabilities; 2) Can recognize authorized usage that falls outside the normal pattern.
Disadvantages: 1) Generally slower, more resource intensive compared to signature-based tools; 2) Greater complexity, difficult to configure; 3) Higher percentages of false alerts.
5) Network Based.
Characteristics: 1) NIDS (network intrusion detection system) examine raw packets in the network passively and triggers alerts.
Advantages 1) Easy deployment; 2) Unobtrusive; 3) Difficult to evade if done at the low level of network operation.
Disadvantages: 1) Fail Open; 2) Different hosts process packets differently; 3) NIDS needs to create traffic seen at the end host; 4) Need to have the complete network topology and complete host behavior; 5) Highly unlikely.
6) Externally Based.
Characteristics: 1) Studies show there are 258 externally measurable characteristics about network infrastructure (without any inside info).
Advantages: 1) Beaching marking – identifying mismanagement symptoms such as poorly configured DNS or BGN networks; 2) Beaching marking – identifying malicious activity which mostly includes SPAM, phishing, and port scanning; 3) One study found it to be highly reliable in predicting breaches (90% true positives in a closed limited test) [3].
Disadvantages: 1) Its low hanging fruit – easy weaknesses to spot; 2) Good I.T. audits and red teaming is similar.
[1] Dash, Debabrata. “Introduction to Network Security”. PowerPoint presentation. 2017.
[2] Photo of public figure Bruce Schneier by Per Ervland. https://www.schneier.com/ 2018.
[3] Liu, Yang; Sarabi, Armin; Zhang, Jing; Naghizadeh, Parinaz; Karir, Manish; Bailey, Michael; and Liu, Mingyan. “Cloudy with a Chance of Breach: Forecasting Cyber Security Incidents” 2015. Pg. 1.

 Ransomware is on the rise and is going after more victims with little to no defenses, small to medium-small sized businesses and even quiet non-profits. Here are a few tools with a valid track record of stopping and removing 3 common types of ransomware.
Ransomware is on the rise and is going after more victims with little to no defenses, small to medium-small sized businesses and even quiet non-profits. Here are a few tools with a valid track record of stopping and removing 3 common types of ransomware. As per Jessica Davis of HealthcareITnews, “SamSam is the virus that
As per Jessica Davis of HealthcareITnews, “SamSam is the virus that 
 A former software developer for Equifax, Sudhakar Reddy Bonthu, faces insider trading charges related to the company’s massive data breach last year, according to the SEC and federal prosecutors. Allegedly, in August 2017, Bonthu was asked to participate in Project Sparta, which Bonthu’s bosses described as a major project for one of the company’s clients who suffered a major breach that exposed details of over 100 million users.
A former software developer for Equifax, Sudhakar Reddy Bonthu, faces insider trading charges related to the company’s massive data breach last year, according to the SEC and federal prosecutors. Allegedly, in August 2017, Bonthu was asked to participate in Project Sparta, which Bonthu’s bosses described as a major project for one of the company’s clients who suffered a major breach that exposed details of over 100 million users.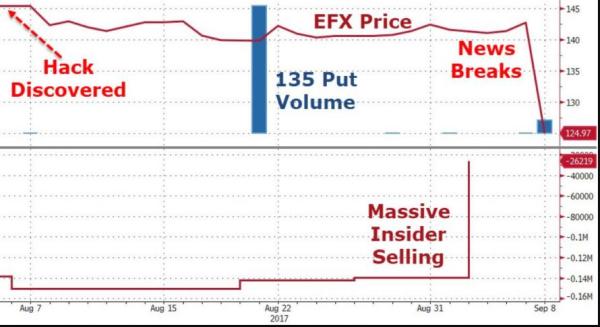
 The first version of the NIST Cybersecurity Framework came about in Feb. 2014. In May 2017 President Donald Trump issued an executive order directing all federal agencies to use the framework to manage this risk, including future versions. Conversely, the private sector more so uses it as a non-uniform guide (sometimes in part) when needed. They use other more industry specific frameworks as well. On 04/17/18 NIST released the updated version of this standard-setting framework. We attended the NIST hosted webcast reviewing this on 04/27/18 and my key points are:
The first version of the NIST Cybersecurity Framework came about in Feb. 2014. In May 2017 President Donald Trump issued an executive order directing all federal agencies to use the framework to manage this risk, including future versions. Conversely, the private sector more so uses it as a non-uniform guide (sometimes in part) when needed. They use other more industry specific frameworks as well. On 04/17/18 NIST released the updated version of this standard-setting framework. We attended the NIST hosted webcast reviewing this on 04/27/18 and my key points are:
 Ransomware continues to be a top cybersecurity threat, according to the report. Ransomware is found in almost 39 % of malware attacks – double the amount in last year’s analysis. “Ransomware remains a significant threat for companies of all sizes,” says Bryan Sartin, executive director security professional services, Verizon. “It is now the most prevalent form of malware, and its use has increased significantly over recent years.” This comes as no surprise to many city and state officials that have battled with ransomware takeovers recently. Systems in the city of Atlanta
Ransomware continues to be a top cybersecurity threat, according to the report. Ransomware is found in almost 39 % of malware attacks – double the amount in last year’s analysis. “Ransomware remains a significant threat for companies of all sizes,” says Bryan Sartin, executive director security professional services, Verizon. “It is now the most prevalent form of malware, and its use has increased significantly over recent years.” This comes as no surprise to many city and state officials that have battled with ransomware takeovers recently. Systems in the city of Atlanta 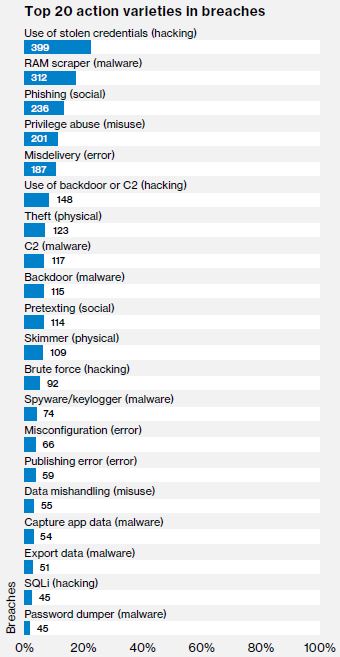 Using stolen credentials topped the list of causes for data breaches (See Fig 1. for the other top causes). A common saying is “it’s easier to ask the employee for their password than try to guess it”, so social engineering continues to be a very useful tactic for hackers. For most employees, the only security protection system is their password. If a cyber-criminal obtains it, they can easily bypass most of the company’s security controls.
Using stolen credentials topped the list of causes for data breaches (See Fig 1. for the other top causes). A common saying is “it’s easier to ask the employee for their password than try to guess it”, so social engineering continues to be a very useful tactic for hackers. For most employees, the only security protection system is their password. If a cyber-criminal obtains it, they can easily bypass most of the company’s security controls.
 The site will serve as my corporate site going forward while the old site:
The site will serve as my corporate site going forward while the old site: 
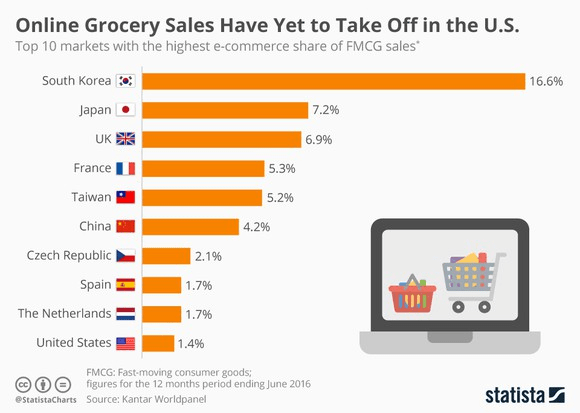


 Minneapolis, MN – 11/22/17. The recent Equifax data breach impacted one-third of the U.S. population with more than 143.5 million records exposed. This epic hack started on 05/13/2017 and lasted until 07/29/2017, all the while the company was clueless. As a result, the threat actors trolled around Equifax’s network, staging and exfiltrating data undetected for 2.5 months. It is one of the biggest data breaches in U.S. history but clearly not the biggest. Going forward, breaches are likely to be bigger, given the threat actors risk vs. reward tradeoff, and the increasing capabilities of cloud computing and botnets thereby enabling anonymity.
Minneapolis, MN – 11/22/17. The recent Equifax data breach impacted one-third of the U.S. population with more than 143.5 million records exposed. This epic hack started on 05/13/2017 and lasted until 07/29/2017, all the while the company was clueless. As a result, the threat actors trolled around Equifax’s network, staging and exfiltrating data undetected for 2.5 months. It is one of the biggest data breaches in U.S. history but clearly not the biggest. Going forward, breaches are likely to be bigger, given the threat actors risk vs. reward tradeoff, and the increasing capabilities of cloud computing and botnets thereby enabling anonymity. Yet this breach may be one of the most negatively impactful because of the comprehensive sensitive data lost in it including social security numbers, full names, addresses, birth dates, and even drivers licenses and credit card numbers for some. “This information is the kind that several businesses like financial companies, insurance companies, and other security-sensitive businesses use to identify a customer accessing their accounts from online, by phone, or even in person”
Yet this breach may be one of the most negatively impactful because of the comprehensive sensitive data lost in it including social security numbers, full names, addresses, birth dates, and even drivers licenses and credit card numbers for some. “This information is the kind that several businesses like financial companies, insurance companies, and other security-sensitive businesses use to identify a customer accessing their accounts from online, by phone, or even in person” 