#realestate #mortgagerates #economics #housingmarket
Fig 1. Housing Decline, Stock Image, 2023.

It’s fair to say there has been a lot of hype and regional bubbles in the real estate market over the last five years. From hyper explosive growth in Denver spurred in part by the marijuana and outdoor recreation sectors to mass biz-tech growth in Austin Texas due to favorable taxes and land plots. Yet part of this has been due to the pandemic mortgage rate decrease, the pandemic drawing out the value of single-family homes, detached townhomes, and/or anything but renting an apartment where contagion spread is more likely. Yet here are five detailed reasons why the real estate market is generally overvalued and headed down soon.
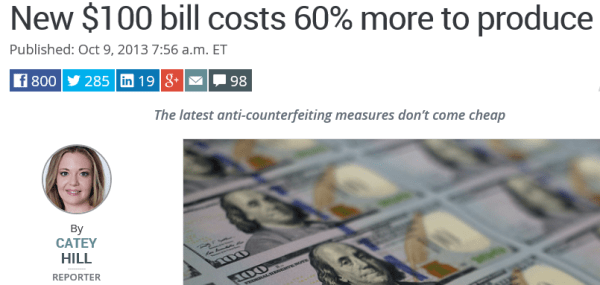
1) For new buyers and those looking to refinance, mortgage rates are still too high. Even with the recent decline from 7.31% to 7.20% on average for a 30-year fixed traditional loan (Yaёl Bizouati-Kennedy, Yahoo Finance, 09/06/23). According to the National Association of Realtors, the average monthly mortgage payment rose 85% in the past 19 months, from $1,212 in January 2022 to $2,246 in August 2023 (US Bank, The impact of today’s higher interest rates on the housing market, 08/30/23). Yet income has not gone up on average enough to get close to matching this payment increase.
2) Most of the people who wanted to move to other cities due to the mass work-from-home shift drawn out by the pandemic have already moved and secured mortgages in the lower 2.25% to 4.50% range. They have little incentive to move again considering higher moving costs and higher mortgage costs. Plus, many of them are now settled down with families and friends and are thus doubly less likely to move anytime soon.
3) Both new purchase and refinancing mortgage application numbers are at a huge 28-year low. “Mortgage applications declined to the lowest level since December 1996, despite a drop in mortgage rates. Both purchase and refinance applications fell, with the purchase index hitting a 28-year low” (Joel Kan, Mortgage Bankers Association, 09/06/23). Additionally, it is not likely to get better anytime soon and has already brought demand down. Slight mortgage rate increases or decreases will not do much to reduce this trend because income has not gone up enough and overall inflation has not decreased enough.
4) The millennial generation on average when compared to other generations is overly individualistic, spends a lot on fancy cars and vanity (YOLO), and does not save much. Thus, this generation has a higher-than-average number of people who will not qualify for a mortgage in this environment at present. The next generation, Zoomers — although generally farther from the homeownership age, are not on track to save either. Both of these generations are on average far worse financial planners than previous generations. “A Bankrate survey observed that 54% of younger millennials and 46% of Gen Z respondents said their emergency savings had declined since 2020. The survey also revealed that millennials were more likely than other generations to have higher credit card debts than savings balances” (Megan Sauer, CNBC, 06/14/2022). What’s the point in saving money if you are an Instagram model or video game streamer? There are no large-scale plans to solve anytime soon by either the government or private sector.
5) Although a study from April 2023 indicated that one-third of home buyers are cash buyers (Al Yoon, Insider, 06/08/23). Yet this cannot logically last with inflation making most things cost more, estate financial transitions, and divorces on the rise taking more of that cash reserve. Cash buyers are running out of cash and there are fewer of them left after the housing boom and bid war from 2018 to mid-2023. The other issue with cash buyers is they need to prove where the cash came from. Sadly, a higher percentage of that is from fraud due to increased crypto money laundering, NFT pump-and-dump scams, and related ventures. With Western authorities cracking down on these fraudsters, their dirty money will less often be used to purchase homes.
About the author:
Jeremy Swenson is a disruptive-thinking security entrepreneur, futurist/researcher, and senior management tech risk consultant. Over 17 years he has held progressive roles at many banks, insurance companies, retailers, healthcare orgs, and even governments including being a member of the Federal Reserve Secure Payment Task Force. Organizations relish in his ability to bridge gaps and flesh out hidden risk management solutions while at the same time improving processes. He is a frequent speaker, published writer, podcaster, and even does some pro bono consulting in these areas. As a futurist, his writings on digital currency, the Target data breach, and Google combining Google + video chat with Google Hangouts video chat have been validated by many. He holds an MBA from St. Mary’s University of MN, a MSST (Master of Science in Security Technologies) degree from the University of Minnesota, and a BA in political science from the University of Wisconsin Eau Claire.


 3) A.I. has the potential to close the gap between the lesser developed world and the developed world. The technology behind A.I. is not limited to big companies like IBM or Microsoft for the long term. We may be surprised with tech start-ups out of the lesser developed world who are very creative. Lack of fiber optic cable connectivity has forced many lesser developed nations to rely heavily on cell tower smartphone based internet communications. This has inspired a mobile app growth wave in parts of Africa as described here; “the use of smartphones and tablets within the country has led to a mobile revolution in Nigeria. Essentially, people now tend to seek mobile solutions more often and thus, enhance the growth of the mobile app development industry” (
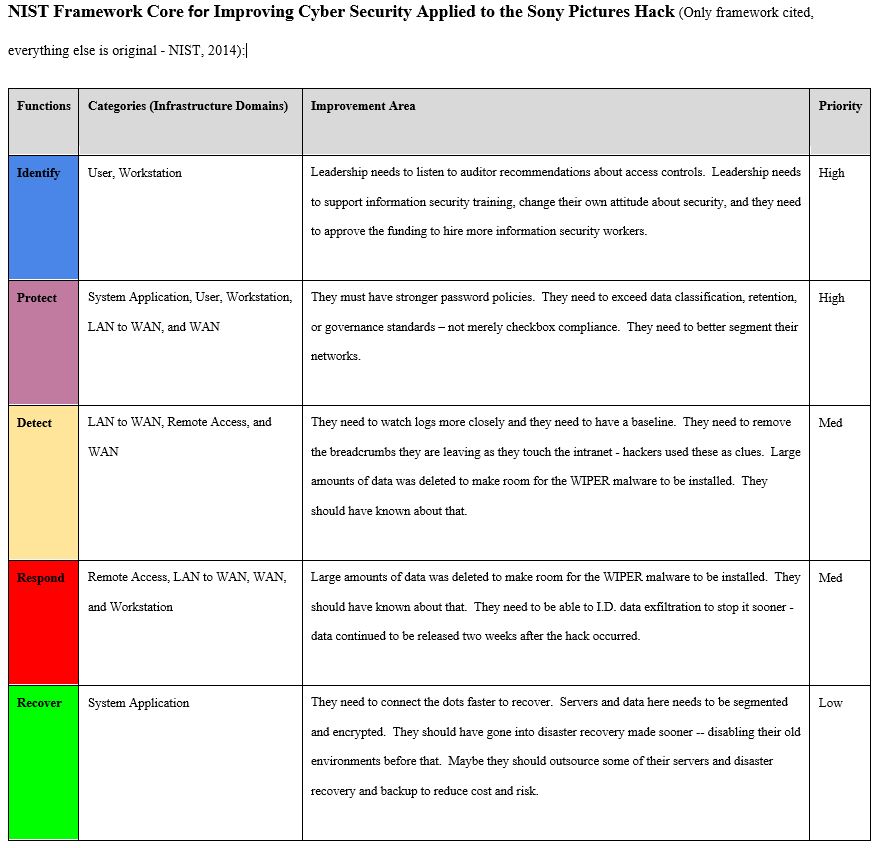
3) A.I. has the potential to close the gap between the lesser developed world and the developed world. The technology behind A.I. is not limited to big companies like IBM or Microsoft for the long term. We may be surprised with tech start-ups out of the lesser developed world who are very creative. Lack of fiber optic cable connectivity has forced many lesser developed nations to rely heavily on cell tower smartphone based internet communications. This has inspired a mobile app growth wave in parts of Africa as described here; “the use of smartphones and tablets within the country has led to a mobile revolution in Nigeria. Essentially, people now tend to seek mobile solutions more often and thus, enhance the growth of the mobile app development industry” ( This article reviews the 2014 Sony hack from a strengths and weaknesses standpoint based on select parts of the SysAdmin, Audit, Network and Security (SANS) and National Institute of Standards in Technology (NIST) frameworks. Although an older hack, the lessons learned here are still relevant today.
This article reviews the 2014 Sony hack from a strengths and weaknesses standpoint based on select parts of the SysAdmin, Audit, Network and Security (SANS) and National Institute of Standards in Technology (NIST) frameworks. Although an older hack, the lessons learned here are still relevant today.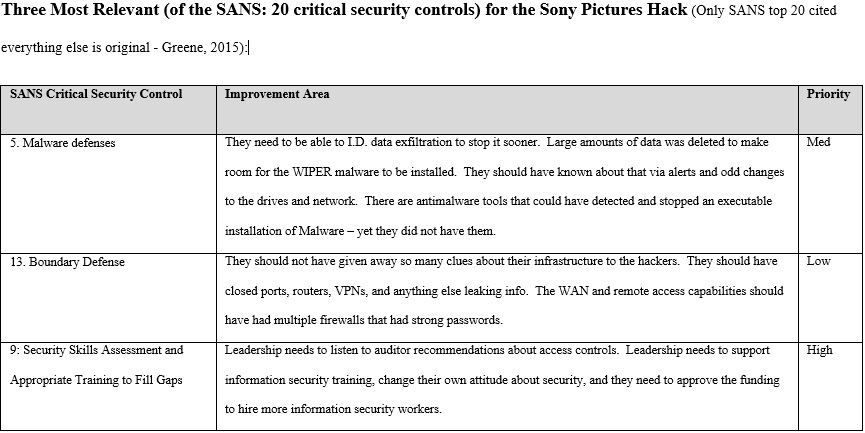
 1) We knew there would come another well-positioned company who makes a pair of smart glasses like Google Glass and that it will derive more competition and innovation. Microsoft raised their hand right away with their HoloLens glasses which are hologram based, slightly “gamified”, and seemingly better than Google Glass largely because they tied it in with known Windows functionality (broader offerings). See a video of this cool new technology here:
1) We knew there would come another well-positioned company who makes a pair of smart glasses like Google Glass and that it will derive more competition and innovation. Microsoft raised their hand right away with their HoloLens glasses which are hologram based, slightly “gamified”, and seemingly better than Google Glass largely because they tied it in with known Windows functionality (broader offerings). See a video of this cool new technology here: There is no doubt that mobile will continue to grow and will be used on smaller devices like watches, ear buds, pacemakers, and contact lenses. Web design has shifted so fast to mobile that sometimes good web design and user experience is forgotten about for non-mobile users or business users who on average spend much more time on those same sites than mobile users. Thus a better balance of the two design types is needed, and an app is a separate project all together yet still needed. I also think Microsoft will take more mobile market share away from Android and Apple since they have learned a lot from their Windows 8 release and are quickly working to release Windows 10 as a better touch based mobility optimized O.S. that many are excited to try.
There is no doubt that mobile will continue to grow and will be used on smaller devices like watches, ear buds, pacemakers, and contact lenses. Web design has shifted so fast to mobile that sometimes good web design and user experience is forgotten about for non-mobile users or business users who on average spend much more time on those same sites than mobile users. Thus a better balance of the two design types is needed, and an app is a separate project all together yet still needed. I also think Microsoft will take more mobile market share away from Android and Apple since they have learned a lot from their Windows 8 release and are quickly working to release Windows 10 as a better touch based mobility optimized O.S. that many are excited to try.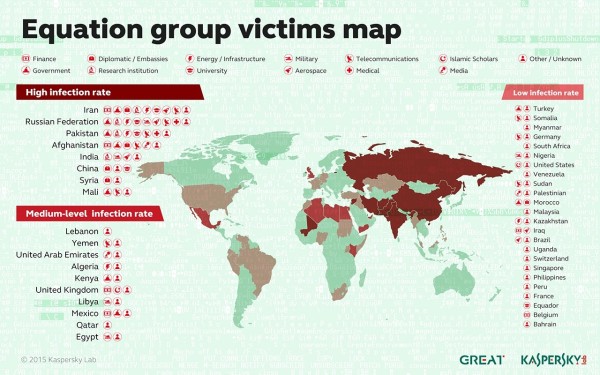
 1) Stakeholder Management: Attain clear support from the executive stakeholders from the beginning of the project and schedule regular check-in meetings with them ahead of time as they tend to be very busy and are often pulled in many directions. Set the tone that their participation is needed and that they will need to approve change requests which is not uncommon. You should also use clever people skills and empathetic listening skills as you interview the many high-level stakeholders in the early part of the project so as to diffuse conflict and get consensus on disagreements about scope, business goals, order, and to find out who will be the thorn in your back as the sooner you know that the better. Also, accept that stakeholders will be different and they may not even directly work for your company which is ok as those ones tend to offer specialized expertise and are often very creative.
1) Stakeholder Management: Attain clear support from the executive stakeholders from the beginning of the project and schedule regular check-in meetings with them ahead of time as they tend to be very busy and are often pulled in many directions. Set the tone that their participation is needed and that they will need to approve change requests which is not uncommon. You should also use clever people skills and empathetic listening skills as you interview the many high-level stakeholders in the early part of the project so as to diffuse conflict and get consensus on disagreements about scope, business goals, order, and to find out who will be the thorn in your back as the sooner you know that the better. Also, accept that stakeholders will be different and they may not even directly work for your company which is ok as those ones tend to offer specialized expertise and are often very creative.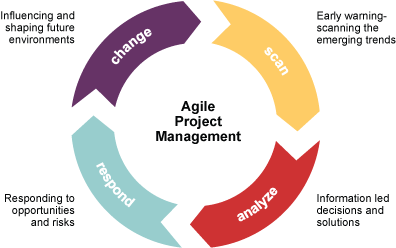 3) Quality Management: Having worked on many complex projects in highly regulated industries over the last 5 years I have noticed a shift towards agile methodologies vs. waterfall. From my perspective this is really about quality and timely flexibility. Aligning the project tasks in small pieces allows you to test the results independently and faster, and if the results are bad that’s a good thing because it’s just one piece of the project and you can learn from it – getting an early warning. Yet to get better quality out of an error you need to have documented what went into the error from beginning to end and you need intelligent consensus. On SDLC projects there will be many small errors which then raise questions about other systems and how they relate to the business rules. Yet with good process flows, screen shots, and JAD sessions with key people, you can ensure that these errors are nothing more than normal bumps in the road. Every project has its bumps but the real test is having above average quality on budget and on time at the projects end thus creating a reusable plan others can learn and be inspired from.
3) Quality Management: Having worked on many complex projects in highly regulated industries over the last 5 years I have noticed a shift towards agile methodologies vs. waterfall. From my perspective this is really about quality and timely flexibility. Aligning the project tasks in small pieces allows you to test the results independently and faster, and if the results are bad that’s a good thing because it’s just one piece of the project and you can learn from it – getting an early warning. Yet to get better quality out of an error you need to have documented what went into the error from beginning to end and you need intelligent consensus. On SDLC projects there will be many small errors which then raise questions about other systems and how they relate to the business rules. Yet with good process flows, screen shots, and JAD sessions with key people, you can ensure that these errors are nothing more than normal bumps in the road. Every project has its bumps but the real test is having above average quality on budget and on time at the projects end thus creating a reusable plan others can learn and be inspired from.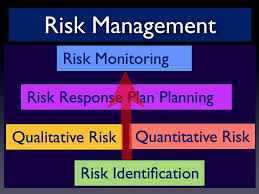 4) Risk Management: In this new era where almost everything is in the cloud and hackers are targeting large and mid-sized companies to steal and sell their data, every risk analysis document/plan should take into consideration data security, customer privacy, access controls from the project team, and there should be an independent audit plan – often out of scope of the project and done by a different group for checks and balances. No project has no data so data is always a part of a project, sometimes more and sometimes less. Question number one is who should have access to the data and at what point? In today’s environment you should embrace a need to know policy and you should document that to reduce risks. You should also imagine a worst case scenario and be prepared for it and run this by the executive project sponsors, and/or risk officer if your company has one.
4) Risk Management: In this new era where almost everything is in the cloud and hackers are targeting large and mid-sized companies to steal and sell their data, every risk analysis document/plan should take into consideration data security, customer privacy, access controls from the project team, and there should be an independent audit plan – often out of scope of the project and done by a different group for checks and balances. No project has no data so data is always a part of a project, sometimes more and sometimes less. Question number one is who should have access to the data and at what point? In today’s environment you should embrace a need to know policy and you should document that to reduce risks. You should also imagine a worst case scenario and be prepared for it and run this by the executive project sponsors, and/or risk officer if your company has one.