1) Russian Hacking in U.S. Elections – critical infrastructure implications:
For more than ten years candidates and advocacy groups have used internet marketing hacks to steal their opponent’s websites, redirect internet traffic, or increase negative search results on them by manipulating search engine algorithms. For example, former GOP Presidential candidate Carly Fiorina failed to register carlyfiorina.org and thus had an opposition group use it as negative publicity against her, but she has since acquired the site. Yet 2016 proved to be a turning point in political hacking because of the level and sophistication and sustained effectiveness. The Washington Post reported, “Russian government hackers were able to penetrate DNC servers, compromising opposition files, chats, and emails on republican nominee Donald Trump (Eliza Collins, 12/30/16, USA Today). With this information, Russian intelligence agents masqueraded as third parties to create very believable spear phishing campaigns. These fake emails worked to trick victims into typing in their usernames and passwords after which Russian agents moved further into their networks, undetected at the time.
On 12/29/16, in a first of its kind move, the Obama Administration released a joint FBI and DHS report (JAR-16-20296: GRIZZLY STEPPE – Russian Malicious – US-Cert) on the technicalities of the hack and sanctioned the GRU and the FSB (Russian intelligence agencies) and key companies they contracted with (Katie Bo Williams, 12/29/16, The Hill). The following diagrams (Fig. 1-a and 1-b) show there were two main hacking groups and that they used mostly classic hacking tactics that were clearly preventable. APT29 hides via encrypted communication and speeds up commands via PowerShell code automation, applied to multiple operating systems. Thus they must have been observing and studying/testing for a while to get this right as its complex across phones, tablets, and PCs. At the same time, APT28 was using a private tunnel (like a VPN) to install and remotely run applications – key loggers designed to steal information and credentials.
Russian DNC Hack Diagram – Fig. 1 – a: (JAR-16-20296: GRIZZLY STEPPE – Russian Malicious – US-Cert).
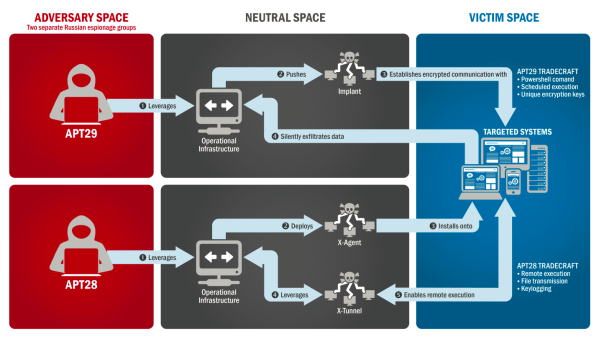
All this started as far back as the summer of 2015, so the full penetration went undiscovered for more than a year. In that time, it has been alleged that the hackers were releasing embarrassing info to manufacture fake negative news against Hillary Clinton. In one instance the release of this info resulted in the resignation of the on DNC Chair, Florida Representative Debbie Wasserman Schultz. Yet the hack is not fully partisan because many sources confirmed that, Republican House members, thought leaders and non-profits to the GOP, were also hacked (Jeremy Diamond, 12/16/16, CNN).
Russian DNC Hack Diagram – Fig. 1 – b: (JAR-16-20296: GRIZZLY STEPPE – Russian Malicious – US-Cert).
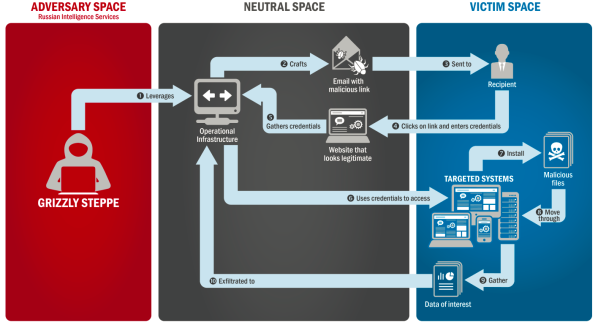
On 12/30/16 the Obama Administration took the strong action of expelling thirty-five Russian diplomats in response to the hack. Shortly thereafter they enacted OFAC (Office of Foreign Asset Control) sanctions against Russian business entities associated with these people. They left the country under close U.S. escort on 01/01/17 as they arrived at an airport to depart on a private Russian plane sent by president Putin.
Alleged Hacker and Russian Spy, Alisa Shevchenko – Fig. 3:
 Interestingly, one of the people expelled, Alisa Shevchenko, was praised a year before by the United States which does not speak well for U.S. intelligence agencies. Specifically, The Department of Homeland Security said “Alisa Shevchenko had helped prevent cyber crime under a program for information sharing between the public and private sector. Ms. Shevchenko was also said to have assisted a French company, Schneider Electric, in identifying vulnerabilities in its software” (Andrew E Kramer, New York Times, 12/31/16). However, we think she may have been a Russian spy all along and could have been inside key U.S. systems at that time but this unconfirmed. Her company, Zora Security, has been a key supplier to the Russian Military’s Main Intelligence Directorate, or G.R.U. In her recent Twitter posts she indicates that she is indifferent to being discovered by the U.S. intelligence agencies. This is likely because she is a close pawn of Putin’s who did a fairly good job going undetected as long as she did. More intel is likely to come out substantiating this.
Interestingly, one of the people expelled, Alisa Shevchenko, was praised a year before by the United States which does not speak well for U.S. intelligence agencies. Specifically, The Department of Homeland Security said “Alisa Shevchenko had helped prevent cyber crime under a program for information sharing between the public and private sector. Ms. Shevchenko was also said to have assisted a French company, Schneider Electric, in identifying vulnerabilities in its software” (Andrew E Kramer, New York Times, 12/31/16). However, we think she may have been a Russian spy all along and could have been inside key U.S. systems at that time but this unconfirmed. Her company, Zora Security, has been a key supplier to the Russian Military’s Main Intelligence Directorate, or G.R.U. In her recent Twitter posts she indicates that she is indifferent to being discovered by the U.S. intelligence agencies. This is likely because she is a close pawn of Putin’s who did a fairly good job going undetected as long as she did. More intel is likely to come out substantiating this.
At present, the election systems aren’t considered among the sixteen U.S. critical infrastructures and thus they have no federal protection. This is because current law defines the administration of elections as in the hand of each state and these states do not want federal involvement into their election systems out of fear of political persecution. We can understand this (especially Texas) but think some compromise could be accorded if a state election system was targeted by a foreign government, thus making it a national interest. The federal government is less involved in the day to day activities and security of the sixteen critical infrastructures because 80% of them are owned by private enterprises. However, when Sony got hacked in 2014 it became a national issue a few days later and then the Federal government helped out, but afterward, Sony quickly wanted to avoid contact with them. This is because, although well intentioned and large, the federal government is not as good at most I.T. security as the private sector is. Yet the case of multiple state election systems is unique because they are used only for elections and then are put in storage. Ultimately each states voting data rolls up to the federal level and most of this supply chain is at risk to hacking and manipulation. Thus, the maintenance and updates of these systems and the systems used by dispersed political parties for campaigns need to be improved. This may require some sort of hybrid-critical infrastructure protection, increased private sector partnership, or just more dollars spent by the state election bodies and political parties. Why are commercial facilities and their systems more important than the systems that track election activity and results in a country that fought several wars to stay democratic? By including the election process and systems as a critical infrastructure or hybrid-critical infrastructure, researchers and entrepreneurs will be inspired to improve the process, all the while sustaining or increasing privacy which is a must for a nation as diverse as the United States. More news outlets, advocacy groups, consultants, and academics need to debate this publicly!
2) Tesla and the Growth of the Electric car – decline of the gasoline based car:
2016 was a profound year of announcements when it comes to the market for electric cars. Many car manufacturers have been playing catch up with Tesla for a few years now. That being said, several companies have produced versions of their own electric car. But there are very few that have produced an electric car designed from the ground up. The Nissan Leaf and BMW i3 were two of those, and as of November 2016 Chevrolet started manufacturing its Bolt EV. Mercedes also announced that it will have several different types of electric vehicles soon. This includes their urban electric-powered straight truck (Fig. 3) which has self-driving capabilities. This would allow inter-city delivery on an EV platform.
Mercedes Electric Self-Driving Truck Prototype – Fig. 3:
 Simply put, the market is starting to catch up to Tesla. 2017, we think will be the year that makes or breaks Tesla. If Tesla can ramp up production like it plans to, it will continue to maintain market share. By 2018, it has audacious production goals of a half million. With just about every major automotive company producing plans for electric vehicles, competition for this segment will start to get really competitive.
Simply put, the market is starting to catch up to Tesla. 2017, we think will be the year that makes or breaks Tesla. If Tesla can ramp up production like it plans to, it will continue to maintain market share. By 2018, it has audacious production goals of a half million. With just about every major automotive company producing plans for electric vehicles, competition for this segment will start to get really competitive.
3) Self-Driving Cars – personal and commercial:
Google has been developing a self-driving car for a few years now, but it has been slow to fully develop and bring them to market. In fact, a few of Google’s employees left to start their own company for self-driving trucks. That company, Otto, was recently sold to Uber for $680 million (Mark Harris, Business Insider – Back Channel, 12/03/16). Uber has also been working on self-driving cars with its Ford Fusion line. Now, these cars still have people behind the wheel just in case of an emergency, but it’s the next step in fully rolling out an autonomous fleet of vehicles. Uber gave their fleet of Volvo XC-90s a try for only a week in San Francisco but picked up and moved on to Arizona to continue testing. This was because they didn’t want to comply with California DMV requirements to file paperwork and pay a registration fee. Otto, on the other hand, also made their first delivery of Budweiser beer in Colorado (Fig. 4).
Otto Self-Driving Budweiser Delivery Video – Fig. 4:
This is dawning the start of Uber Freight where shippers can ship through an Uber App for their truckloads. C.H. Robinson and Amazon are both developing apps like this. We think before cars get the green light to drive in inner-cities, self-driving semis will get the regulatory green light, firstly on interstates. This is because commercial vehicles cost a lot more, are bigger, serve thousands of customers per year, thus the investment in self-driving technology is a justified priority in spite of any risk. Additionally, commercial shipping is automated in most parts of the supply chain and this is a precursor for self-driving trucks. The NHTSA did publish guidelines on self-driving cars and their testing in September (link here). We think 2017 will be the year of testing self-driving vehicles and in 2018 it will start to become a mass market idea.
4) Surveillance via Smart Phones – privacy implications:
Smartphones are small supercomputers that house more personal info on their users and families than any other device in modern history. From texts, PHI, fingerprint scans, downloaded documents, contact lists, photos, geolocation tags, the use of many cloud databases – both upload and download, and apps that take away some of our privacy – via partial and full consent. A smart phone is more advanced than any gadget dreamed up by 007 and the need for privacy on it is just as important.
2016 proved to be a turning point in the privacy vs. government surveillance debate. It intensified after the mass shooting in San Bernardino, CA, which happened at the end of 2015, killing 14 people. Then in 2016 the government sued Apple to get them to build a backdoor into the perpetrators iPhone to which Apple strongly objected. The government eventually broke into them phone shortly thereafter with the help of Israeli tech contracts. Keep in mind that ever since Edward Snowden leaked NSA documents in 2013 about the government’s overreach into technology companies, to get them to build back doors, it has become more politically acceptable to resist such demands. Congress has made very minor surveillance rollbacks, mostly related to phone metadata but much more work needs to be done (Ellen Nakashima, The Washington Post, 11/27/15).
Andriod phones have also suffered hacks and backdoors. A source described it this way, “security experts say they have discovered secret ‘backdoor’ software in some Android phones that sends users’ personal data to China. Kryptowire, the security firm that discovered the vulnerability, confirmed this information on its website on Tuesday. The firm wrote that certain Android devices contain pre-installed software that collects and sends personal data, such as texts and geographical location, to an unauthorized third-party” (New York Times, 11/15/16). This is a clear blow to android privacy and will require costly R&D by Google. With the growth of third party phone applications these risks will continue to increase and get more complicated.
Illustration of Apple vs. The FBI – Fig. 5:
 Although the government argues that back doors make the nation safer, this makes no logical sense and there are no real world case studies to support it. First of all, the fact that the government needs to rely on the private sector for such backdoors and tech consulting proves that the private sector is where technology innovation comes from and that supports the concept of intense free competition.
Although the government argues that back doors make the nation safer, this makes no logical sense and there are no real world case studies to support it. First of all, the fact that the government needs to rely on the private sector for such backdoors and tech consulting proves that the private sector is where technology innovation comes from and that supports the concept of intense free competition.
The U.S. intelligence agencies would not be much better than a “drunken inspector gadget” without third-party consultants and tech firms. Key private sector innovation in the military industrial complex has helped this nation win wars and secure freedom for all – way back to the founding of the Union. This includes stealth fighter technologies, radar technologies, canons, and it does not require government overreach or back doors. The government is a paying customer of the best tech products and has always been.
Yet when the same consultants and tech firms serve regular customers, like Apple with the iPhone, those customers have a reasonable expectation of privacy and quality. This should not diminish merely because the government can’t solve a crime or problem quickly. Apple CEO Tim Cook described the government’s request this way, “it’s the software equivalent of cancer. He said he was prepared to take the fight all the way to the Supreme Court. This would be bad for America, he said. It would also set a precedent that I believe many people in America would be offended by” (Enjoli Francis, ABC News, 02/24/16). There are far more security benefits in keeping private technology data private. This includes privacy after domestic breakups, privacy from cyber-stalking, privacy from annoying marketing, privacy from political persecution and harassment. Also, Government agencies can use these same private technologies to conduct military and intelligence operations without worrying about being hacked by opposing governments or terrorists.
In 2017 we think technology companies will increase the security of their products, and companies like Apple and Google are already in the process of doing this. In Apple’s case, they have spent millions to hire encryption legend Jon Callas, who invented PGP encryption, to redesign the security of their products (Reuters, 05/24/16). We think most company shareholders, investors, customers, and finance people now see the additional cost to build in great security as required. To customers, security on a product is worth a price premium and a globally competitive company must have secure products.
We also think policy makers will have to do more to accommodate the privacy concerns of citizens, perhaps partly like the E.U. has done. We also think 2017 will further debunk the connection between backdoor system hacks and terrorism prevention. Clearly, monitoring the entire free world’s metadata is a violation of democratic norms, and it waters down security greatly because it can easily be manipulated for every imaginable bad reason. Most likely, setting people up, and government leaders throughout all history like to find people to blame for their problems/misdeeds. Yet behavioral profiling and good traditional police and intelligence work in conjunction with advanced sustained diplomatic dialogue with a range of diverse groups, friends and enemies alike, should produce better intelligence for more specific actionable results. The intelligence community has thousands of tech tools to use to secure the nation, mostly private sector based, so they don’t need to monitor all metadata.
5) Using Drones for Last Mile Deliveries – suited for rural and high traffic areas:
Amazon Prime Drone via Prime air – Fig. 6:
 Amazon made its first test delivery by a drone in the U.K. in 2016. This will continue to be developed as Amazon continues to test and tweak its system for making deliveries by drone. In fact, this is one of many programs where Amazon is developing its systems in “last mile” delivery. They also currently have their own fleet of vans to deliver and they use their Flex program of drivers to pick up and deliver packages. They also recently filed a patent for “floating warehouses” where these would have inventory in an airship that drones could pick up products and then deliver them, for example to a sporting event (Kate Abbey-Lambertz, 12/30/16, Huffington Post). Realistic but far out innovation like this will continue to challenge UPS and FedEx to provide a better customer experience. Drone delivery is just one idea. The benefit or idea behind drone delivery is that it could deliver to customers within a half hour. This would drastically improve the time to deliver to its customers. Currently, with Prime Now, you can get one-hour and two-hour delivery in certain areas.
Amazon made its first test delivery by a drone in the U.K. in 2016. This will continue to be developed as Amazon continues to test and tweak its system for making deliveries by drone. In fact, this is one of many programs where Amazon is developing its systems in “last mile” delivery. They also currently have their own fleet of vans to deliver and they use their Flex program of drivers to pick up and deliver packages. They also recently filed a patent for “floating warehouses” where these would have inventory in an airship that drones could pick up products and then deliver them, for example to a sporting event (Kate Abbey-Lambertz, 12/30/16, Huffington Post). Realistic but far out innovation like this will continue to challenge UPS and FedEx to provide a better customer experience. Drone delivery is just one idea. The benefit or idea behind drone delivery is that it could deliver to customers within a half hour. This would drastically improve the time to deliver to its customers. Currently, with Prime Now, you can get one-hour and two-hour delivery in certain areas.
We think Amazon will continue to develop its drone delivery in 2017 by testing it in many countries across the world. The FAA in the U.S. has been one roadblock to Amazon testing in the United States. This is just one agency that is figuring out how to regulate this new technology as it tries to prevent small planes and traffic from colliding with drones. Amazon’s competitors are watching and we’ll see how far they get in 2017.


Jeremy Swenson and Mike Cassem are two seasoned, part-time, Intel certified, retail technology marketing and training representatives on assignment at Best Buy for clients including Intel, H.P., Trend Micro, Adobe, and others – presently on sabbatical. They also spent five years crafting their public speaking and writing skills in Toastmasters International. For full-time work, Swenson doubles as a Sr. business analyst, process improvement and project management consultant. While Cassem doubles as a marketer and sales logistics analysis consultant. Tweet to them @jer_Swenson and @micassem.

 Windows 10 also introduces a function that allows you to utilize multiple desktops not just screen extensions, and this is a lot like Mission Control from Apple OS X. This will be a big benefit for business users, creative users, students, and people who do a lot of multitasking. The hot key shortcut to open a virtual desktop is: Windows key + Ctrl +D. Windows 10 also adds something new for gamers and graphics focused users, direct X12, which is a Microsoft proprietary graphics card decoder that communicates with and optimizes the many different graphics chips on thousands of computer models. It is the industry standard and that is why it’s used on the hugely popular X-Box. Windows 7 and 8.1 will not get access to direct X12 so graphics will be better on Windows 10. A creative person could even game in one desktop while they work in another assuming they have the RAM and CPU power needed for those specific applications – this is pretty cool. Another interesting visual add is the Windows Snap feature which allows you to split your screen into two, three or four separate areas and the hotkey shortcuts for this are:
Windows 10 also introduces a function that allows you to utilize multiple desktops not just screen extensions, and this is a lot like Mission Control from Apple OS X. This will be a big benefit for business users, creative users, students, and people who do a lot of multitasking. The hot key shortcut to open a virtual desktop is: Windows key + Ctrl +D. Windows 10 also adds something new for gamers and graphics focused users, direct X12, which is a Microsoft proprietary graphics card decoder that communicates with and optimizes the many different graphics chips on thousands of computer models. It is the industry standard and that is why it’s used on the hugely popular X-Box. Windows 7 and 8.1 will not get access to direct X12 so graphics will be better on Windows 10. A creative person could even game in one desktop while they work in another assuming they have the RAM and CPU power needed for those specific applications – this is pretty cool. Another interesting visual add is the Windows Snap feature which allows you to split your screen into two, three or four separate areas and the hotkey shortcuts for this are: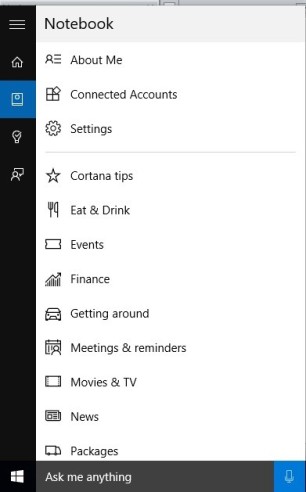 After upgrading to Window’s 10, we weren’t sure if we would use Cortana, but the more we use it the more we like it. In playing around with Cortana, you can provide feedback with screenshots that go right back to the teams at Microsoft. To prepare for the 10 release Microsoft was using an estimated five million external testers known as “insiders” to get this type of bug feedback. This impressive number is a considerable increase from prior releases. Cortana is easy to locate in the bottom left of the screen next to the start menu. We find that if the user types a question in the search bar it will add tips and give you interesting facts each and every day, if you let it. Cortana starts out giving you information on the weather, finance, and sports but you can customize this under notebook settings (Fig. 3). Cortana is very intuitive and can track things for you. If you’re receiving a package, it will tell you the progress or details of that package. Say you’re picking someone up at the airport, Cortana will tell you if the flight is on time.
After upgrading to Window’s 10, we weren’t sure if we would use Cortana, but the more we use it the more we like it. In playing around with Cortana, you can provide feedback with screenshots that go right back to the teams at Microsoft. To prepare for the 10 release Microsoft was using an estimated five million external testers known as “insiders” to get this type of bug feedback. This impressive number is a considerable increase from prior releases. Cortana is easy to locate in the bottom left of the screen next to the start menu. We find that if the user types a question in the search bar it will add tips and give you interesting facts each and every day, if you let it. Cortana starts out giving you information on the weather, finance, and sports but you can customize this under notebook settings (Fig. 3). Cortana is very intuitive and can track things for you. If you’re receiving a package, it will tell you the progress or details of that package. Say you’re picking someone up at the airport, Cortana will tell you if the flight is on time.
